- support@locusassignments.com
Unit 36 Internet Server Management Sample Assignment

TASK 1
Critically evaluate the following Internet technologies and communication protocols
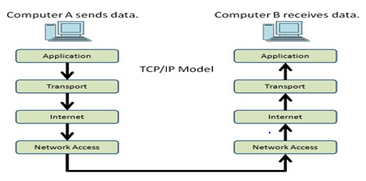
TCP/IP:
TCP stands for Transmission Control Protocol and IP stands for Internet Protocol suite. The TCP is one of the core protocols of IP and is so common that the entire suite is often called TCP/IP. It provides ordered, reliable and error checked delivery of a stream of octets between programs running on computers connected to a local area network, intranet or public internet. It is widely used by the web browsers to connect to the server on the World Wide Web. Also it is used to deliver email an transfer files from one location to another. TCP encapsulates various protocols like HTTP, HTTPS, SMTP, POP3 IMAP, SSH, FTP, Telnet, etc.
OSI:
OSI stands for Open Systems Interconnection model. It is a conceptual model that characterizes and standardizes the internal functions of a communication system by partitioning into abstraction layers. This model consists of seven logical layers. This layers are Physical layer, Data Link Layer, Network layer, Transport layer, , Session layer, Presentation Layer, Application Layer(OSI Model, 2015).
Presentation Layer and Application Layer
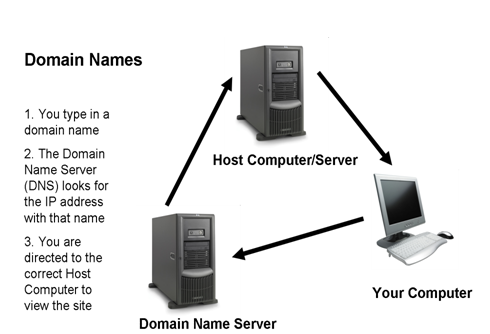
DNS:
DNS stands for Domain Name System is a hierarchical distributed naming system for computers, services or any resource connected to the Internet or private network. The DNS serves domain names and mapping those names to IP addresses by designative authoritative name servers for each domain.
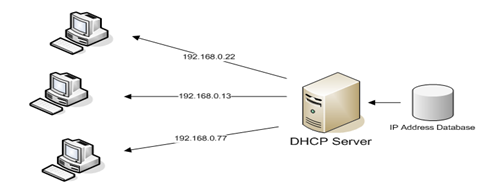
DHCP:
DHCP stands for Dynamic Host Configuration Protocol. It is used on Internet Protocol networks for dynamically distributing network configuration parameters such as IP addresses for interfaces and services. Computers use DHCP for requesting IP addresses and networking parameters automatically from DHCP server, reducing the need for a network administrator.
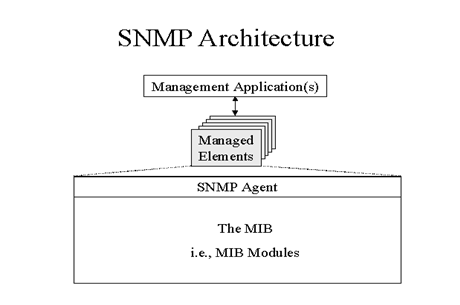
SNMP:
SNMP stands for Simple Network Management Protocols. It is an Internet Standard protocol for managing devices on IP networks. It is used mostly in network management systems to monitor network-attached devices for conditions that warrant administrative attention. It includes routers, switches, servers, workstations, printers, modem racks.
Routing and Remote Access:
Routing and Remote Access Service (RRAS) is a Microsoft API and server software that makes it possible to create applications to administer the routing and remote access service capabilities of the operating systems to function as a network router. It can also be used by developers to implement routing protocols. It can be used to create client applications.
Telnet:
It is a network protocol used on internet or intranet (local area networks) to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection. It actually helps to provide an access to CUI or GUI on a remote host.
Ports:
In TCP layer each message is to be assigned to a port number. By using port number it can determine the type of service being provided. These are not hardware control ports these are just a reference numbers used to define a service. Like, for an example port 23 is used to provide telnet services and port 80 is used by HTTP for providing web browsing services.
Addresses:
These are used to locate computers on a network. To address computers a numbering system is used to help the sender to send the data packets. This numbering system is assigning IP addresses to the computers without the IP addresses it is not possible to send the data packets on a network to a particular requested computer. There are versions of it first is IPv4 another one is IPv6.
ICANN:
ICANN stands for Internet Corporation for Assigned Names and Numbers. It is a non-profit organization that is responsible for the coordination of maintenance and methodology of several databases of unique identifiers related to the namespace of the Internet, and ensuring the network’s stable and secure operation. It mostly concerns on Internet’s global Domain Name System, including policy development for internationalization of the DNS system. IPv4’s and IPv6’s address spaces of the Internet Protocol are the numbering facilities managed by it.
IEEE:
IEEE stands for Institute of Electrical and Electronics Engineers. It is world’s largest association of technical professionals. Its main objectives are the educational and technical advancements of electrical and electronic engineering, telecommunications, computer engineering, and allied disciplines.
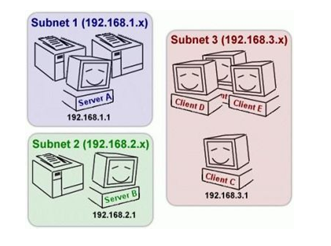
Subnetting:
Subnetting means dividing a network into two or more networks or sub-networks. A sub network is a logical or physical subdivision of an IP network. The most significant group of bits of their IP addresses are identical of the devices which shares the same network. In it the division of IP addresses occurs into two fields, first a network prefix, another as a host identifier.
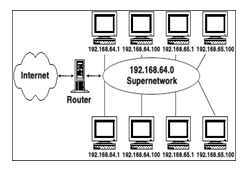
Supernetting:
The process of combining of two or more networks together with a common Classless Inter-Domain Routing (CIDR) prefix. These methods of combining networks together are known as supernet.
Critically evaluate the following Internet services:
Intranet:
It is a computer network used to share information, operational systems or computing services within an organization.
Email:
Email is a method of exchanging digital messages from an author to one or more recipients. Across the internet or other computer networks
E-Commerce:
It stands for electronic commerce in which trading of products and services are done using computer networks such as Internet. Example of famous E-Commerce website is Amazon, Alibaba, etc.
Instant Messaging:
It is an instant text transmission over the Internet it is a kind of online chat. In these two parties are involved and bidirectional transmission of text is being done.
Wiki:
It is a web application which allows collaborative modification, extension or deletion of its content and structure. It is a type of content management system which differs from a blog or most other such systems in which the content is created without any defined owner or leader.
Blogs:
Blogs are a discussion or informational site published on the World Wide Web. These are shown in reverse as the last update appears on top and also contains pictures, videos, etc.
Certificate Services:
These services validate or certify keys as part of a Public key infrastructure using certificate servers. The purpose of this process is to communicate and be reasonably sure that others are not eavesdropping or assuming a false identity.
Directory Services:
It is a software system that stores, organizes and provides access to information and technology in a computer operating system’s directory.
Internetworking Servers:
It is a practice of connecting a computer network with other networks through the use of gateways that provide a common method of routing information packets between the networks. The resulting system of interconnected networks is called an internetwork or simply an internet.
WWW:
It is an information system of interlinked hypertext documents that are accesses via the internet.
FTP:
It stands for File Transfer Protocol and used to transfer computer files from host to another host over a TCP-based network, such as the Internet. It is built on a client server architecture and uses separate control and data connections between client and the server.
Database Servers:
It is a computer program which provides database services to the other computer programs or computers, as defined by the client-server model.
E-Commerce Servers:
It is a web software which runs some of the main functions of an online storefront such as product display, online ordering, and inventory management.
News servers:
A news server is a set of software used to handle Usenet articles. It may aso be the computer itself which handles Usenet solely.
Email servers:
Email servers stores and forwards email messages using several protocols including SMTP, POP and IMAP. Where SMTP is used for sending messages, POP3 is used for retrieving messages. IMAP handles messages and allows a user to browse and manage files remotely.
Proxy Servers:
It is an intermediary between a network hosts outside the network. Its core responsibilities are to provide enhanced security, manage TCP/IP addresses, and speed access to the internet by caching server functions for frequently used documents.
Media Servers:
It offers streaming audio or video over the network. Generally these servers use UDP ports and buffering to achieve the effect of a real-time connection.
Directory Servers:
It provides a central repository for storing and managing information. It can store almost any kind of information from identity profiles and access privileges to information about application and network resources and network devices.
Discuss the following Networking technologies and concepts:
Hubs:
Hubs are the devices which consists of multiple ports and are used for connecting various segments of LAN. Whenever a packet arrives at any port, it is copied to the other ports so that all segments of LAN can see all packets.
Switches:
Switch is used to filter and forwards the data packets between LAN segments. These operates at DATA Link Layer of OSI Reference model.
Routers:
It is a device that forwards data packets along networks. A router is connected to at least two networks, these networks may be two LAN’s or WAN’s. Routers are connected at gateways, the places where two or more networks connect.
Network Management Concerns:
There are major concerns of in network management and that are:
Flexibility vs. Security: The network which is to be developed should be flexible enough to serve the users properly and productively. And hence by increasing the flexibility security levels decreases. So to maintain both at a time a proper development plan is to be build up taking care of both.
Cost vs. Capability: The network should be cost effective to keep in mind the budget of implementing it and also it should be also capable of serving the needs of it users efficiently.
User Group Management:
In this section we consider about managing the rights or permissions granted to the users or groups. In this group is a virtually considered as a particular category of users. They are granted or assigned permissions on which they are bound on that network.
Resource Management:
Resources of networking should be managed in an efficient and best optimized way as it costs really high and provides user a way to communicate to the other in that network. So this is compulsory for the network resources to be used in a much optimized way.
Security:
Security of networks is the first thing which comes into mind when implementing a network. As the network can be hacked by the unauthorized person or group of persons who can harm the users of network by any way. So network security should be kept in mind while implementing any network.
Network Attacks:
Without security measures and controls the network can be attacked by any one. These attacks can harm your data by modifying, deleting, or accessing unauthorized content in it.
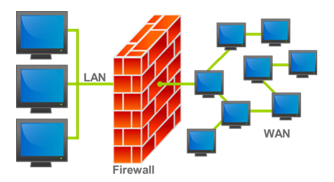
Firewall:
It is a network security system which controls the incoming and outgoing network traffic based on an applied rule set. It establishes a barrier between a trusted secure internal network and another network that is assumed not to be safe.
Servers and their performance:
Servers are expensive, high performance machines. So getting most out of these machines and keeping them running smoothly is critical to maximizing their value. However, maintaining high levels of server performance and keeping those up with growing demands of computing help is the basic requirement. Server performance is a measure calculated by following figures like resource management, optimization performance.
User Access Issue:
To manage user accesses NAC is an approach used in which users are assigned accesses to data according to the network administrator. And also authentication is required in it to access its data.
Critically evaluate the importance of OSI 7 Layer Reference Model
Importance of OSI layer model:
- Reduces complexity.
- Standardizes Interfaces.
- Facilitates modular engineering.
- Interoperability between Vendors.
- Ensures interoperability between Vendors.
- Accelerates evolution.
- Simplifies teaching and learning.
Importance of Layers:
- Layer 7: Provides services directly to user applications. Because of the potentially wide variety of applications, this layer must provide a wealth of services. Among these services are establishing privacy mechanisms, authenticating the intended communication partners, and determining if adequate resources are present.
- Layer 6: Performs data transformations to provide a common interface for user applications, including services such as reformatting, data compression, and encryption.
- Layer 5: Establishes, manages and end user connections and manages the interaction between end systems. Services include such things as establishing communications as full or half duplex and grouping data.
- Layer 4: Insulates the three upper layers, 5 through 7, from having to deal with the complexities of layers 1 through 3 by providing the functions necessary to guarantee a reliable network link. Among other functions, this layer provides error recovery and flow control between the two end points of the network connection.
- Layer 3: Establishes, maintains, and terminates network connections. Among other functions, standards define how data routing and relaying are handled.
- Layer 2: Ensures the reliability of the physical link established at Layer 1. Standards define how data frames are recognized and provide necessary flow control and error handling at the frame level.
- Layer 1: Controls transmission of the raw bit stream over the transmission medium. Standards for this layer define such parameters as the amount of signal voltage swing, the duration of voltages (bits), and so on.
Explain how the OSI (Open Systems Interconnection) reference model relates to the TCP/IP Protocol Model.
OSI models relate to TCP/IP model:
1 TCP/IP Model Layers 2. OSI Model Layers
RJ45:
Here RJ stands for registered jack. And RJ 45 is a connector which is standardized connector used with eight conductors. This connector is used for modem and data interfaces. It looks similar to RJ-11 used to connect telephones.
3 RJ-45 Connector
RJ-11:
It stands for Registered Connector 11. It is a telephone interface that uses a cable of twisted wire pairs and a modular jack with two, four or six contacts. It is the common connector for pluging a telephone into the wall and the handset into the telephone.
4 RJ-11 Connector
IEEE 80X.X:
IEEE stands for Institute of Electrical and Electronics Engineers. It is world’s largest association of technical professionals. Its main objectives are the educational and technical advancements of electrical and electronic engineering, telecommunications, computer engineering, and allied disciplines.
IEEE generalizes its society into different families which are dealing on different topics. Like for example IEEE 802 refers to a family of IEEE standards dealing with LAN (Local Area Network) and MAN (Metropolitan Area Networks). And also there are sub families of IEEE 802 divided like IEEE 802.1 which deals in bridging and network management. IEEE 802.2 deals in LLC. IEEE 802.3 deals in Ethernet. IEEE 802.4 deals in Token Bus. And many more.
Similarities between the two:
- Both have comparable transporrt and network layers.
- Both have application layers though they include very different services.
- Packet switched technology is assumed.
Differences between the two:
- TCP/IP combines the presentation and session layer issues into its application layer.
- TCP/IP combines the OSI data link and physical layers into one layer.
- TCP/IP protocols are the standards around which the Internet developed, so the TCP/IP model gains credibility just because of its protocols, even though everyone uses the OSI model to guide their thinking.
- Packet-switched technology is assumed.
TASK 2 (LO2: 2.1, 2.2, and M2 )
Critically analyse different Internet server technologies:
Server Architecture:
A server exists to provide services to its clients. Workloads vary and an architecture designed to efficiently support one class of applications could be very different from that needed by another class. For economic reasons, a manufacturer wishes to minimize the number of system components it needs to create, maintain and support. The manufacturer builds many different configurations from a reasonably small number of components or subsystems, allowing them the freedom to update one subsystem class without having to update all. A key capability for useful server architecture is an appropriate degree of compos ability – the ability to structure or configure servers by simply connecting various mixes of subsystems.
For this to be possible, a server must be constructed from a number of reasonably independent subsystems connected using a relatively small number of interconnects. Interconnects used to couple very high performance subsystems – such as the processor to its cache or multiple processors to each other – have many more constraints and demands than those needed to hook up slower devices, such as disks. Generally, the intimate high performance interconnects are proprietary (private to the vendor) and tuned for a specific purpose, while those further out toward the edge of the system are more likely to adhere to standards. We will discuss key interconnects and the principles behind them in the next section.
Server Structure:
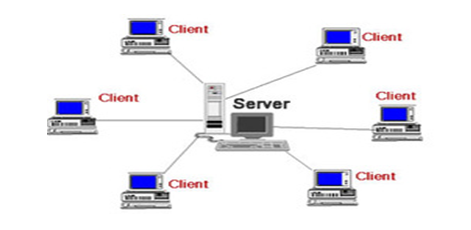
The server structure consists of the client-server model which is a distributed application structure. In it the tasks or workloads are partitioned between the providers of resource i.e. clients and servers. Clients and servers communicate over a computer network on separate hardware but they can also reside on the same hardware. Server shares its resources between the clients but clients do not share any of its resources. Client only requests for server’s content or a service function.
Basic Functionalities of Server:
In today’s time servers perform a lot of tasks but the basic functionalities which every server serves are:
- Host Websites
- Gaming
- Data Storage
- Running Enterprise applications
- Handling Email
- Handling FTP
Request Handling mechanisms:
Usually server handles requests of multiple clients at a time. And the steps which it follows are following:
- First of all, clients sends a request for accessing or connecting to the network, server primarily authenticate that the user is valid by using its user name and password. If user is authenticated it is allowed to access the network.
- Now, the client can access the content. And according to its privileges it can work on it.
- Client sends request to server and server responds to it by processing on its request.
- At last, whenever the client exits the server closes its session and quits.
Performance Issues of IIS and Apache:
Performance and security improvements have meant a lot to IIS. It has improved and gained its share on Apache, from about 21% in 2010 to about 32% as at Feb 2014. It also is vulnerable to the infamous Code Red worm, it has given a lot to significant gain to security. Whereas IIS is not yet perfect, for instance it has been proved poor at supporting PFS (Perfect Forward Secrecy) which is a property of cryptography.
Apache also utilizes external web extensions to implement some features. It has low costs as compared to IIS. And its performance is better as compared to IIS in terms of performance.
Both of them have advantages and disadvantages as mentioned above. For choosing any of the one depends on various factors. In case of IIS which can be bundled with Windows whereas Apache does not have big-name corporate support, Apache has excellent security but does not support .NET support which IIS does.
Discuss the Hardware and software required components of a Web Server.
Hardware and Software requirements of Web Server
The requirements of hardware and software of web server depends on the requests which the web sites on it get on a per day basis. Here we consider that our web server serves 1000requests/day. So according to it our configurations are:
CPU: The server’s CPU should be of the configuration 8 * 3.0 GHz or higher speed quad core processor. The CPU is very important aspect in any server as it has to be fast and efficient to serve the requests of clients as fast as possible. This mentions the efficiency the server.
The client’s CPU should be of the configuration 3.0 GHz or higher dual core processor.
Memory: Here memory specifies the temporary memory of the server or the RAM. So in our requirement it should be at least 16GB to 32 GB. AS the web server has to hold the status of clients in RAM. Their status are stored as sessions in the web server. And web server holds them only for the time in which they are logged in. And for that time the sessions are stored by web server on the server RAM. So the RAM should have enough capacity to hold the sessions of all clients logged in at a time. As well as the RAM is also used by the server to process the requests from all the clients at same time.
The client’s specification for memory should be at least 1.5 GB to 4GB for using the web server or matching the speed of web servers.
Storage Devices: Storage devices are the primary parts required in Database servers as it has to store data in a very big amount but in web servers the storage capacity is not given the weightage as the processing unit as it has to only store data related to the web services provided by the server or data containing information technology or databases used by web services.
In our case the server should at least hold 1TB to 2TB for storing the data related to web services provided by the web servers. And also there should be some amount of free space present in client’s computer for using the web services. This space can be 100GB to 200GB.
Operating System: There are special operating systems on which the web server should be implemented. In our situation we can use any of the one from:
- Red Hat Linux 5.2, x64 Edition
- Fedora 14 x64
- Windows Server 2003
- Windows Server 2008
Operating system helps to interface between the hardware and software of the computer. Here in web server specific application related to web service are efficiently managed and executed by special operating systems like mentioned above. Operating systems used by the clients do not require any special feature like operating systems of servers. So we can use operating system from any below:
- Windows XP, SP3+
- Windows Vista
- Windows 7 x86, & x64
- Mac OS X
Software Requirements:
There are some software requirements which should be fulfilled to implement a web server. As for interfacing software’s are required and also to implement any web service it is compulsory. So for implementing a web server the software which is necessary the most is web server itself. So here in our scenario we install IIS as a web server which is used as an interface to implement web services and act as a web server. In this all the processes of Web Server are done by IIS the implementation of any web service is very easy using it as you can specify anything you want to do in or with your web application in it using a simple GUI of IIS.
Another software is Java with its latest version which is used to run our compile our web application or service on a web server. Some more soft wares are there like MySQL for managing databases in our web applications.
The software components which are required by the client are just Browser to use web services or applications on its computer.
Cost of Running an Internet Server:
The total cost for running an Internet Server consists of submission of following costs:
- DNS Hosting cost
- Hardware Cost
- System Setup cost
- Software Cost
- SSL
- And many more
TASK 3 (LO3: 3.1 and 3.2)
Develop a detailed, well-designed deployment Plan that will allow organizations to maintain secure configurations and aids in identifying security vulnerabilities.
Primarily, a server can be defined as the host that accommodates services to many other hosts throughout the network, this is the primary function of a server, like a file server facilitates the capabilities of file sharing across other host so that other user can perform various operations on files like deleting, modifying etc. Another good example can be a database server that facilitates database related services for the Web applications running on the Web servers and the web servers in turns provides web contents to the clients that is the web brewers that user uses to request for a web page from the web server.
We should consider security vulnerabilities and threats to make a web server secure and for this it is must to define the kind of threats that must be reduced. Knowledge to such kind of threats are necessary to take security measurement to make the server secure. there are many kind of threats that can be possible against the data and resource available on the server and that can be either bugs in the operation system or any kind of bug in the server software that can highly enhance the create a security vulnerability. Threats may include the attackers that is trying to access the resources and data available on the server or the administrator that mistakenly forgets to disable the user accounts an ex-employee that has leave the organization. Threats can be of any type and can be from local network such as a displeased or dissatisfied employee, or they can be from remote network for example a remote attacker from any other location and from other network.
Attackers can use many different ways through the application to harm to our organization or business. Each of the way denotes a high risk that may not or may be serious enough to grab our attention.
In computer world and computer system networking, basically a network service is a program of application that is running at the application level and above, it basically provides storage of data, manipulation of data and communication that is implemented using a client-server model based application. A web server provides many service that are actually presented as the components of a server. These can be easily accessed by its clients and can work on more than one computer at a time. But it is not necessity though to employ different machines for clients and servers respectively as simultaneous operations can take place on a particular system. Moreover, both the client and server have been using user interface with the association of other hardware as well.
Explain and implement the following Installation technologies: tools eg GUI (Graphical User Interface) and command line; activities eg create website, create virtual directory, install FTP services, and create FTP sites
When we want to make our website public and accessible to all users across the internet, we have to create a website under the web server to store and hold the contents to the web site. When we install IIS, it automatically creates a default web site configuration in the /Inetpub/wwwroot directory. This default directory may be utilized in order to publish the content on website; moreover, this can be also be used in order to form a directory at a desired location of files and folders. On creation of a new website in IIS, the entry can be created in ApplicationHOst.config file. The entry represents the binding of the website and also scales the mapping of the website to a chosen directory. Moreover, through its deployment, one can opts up for the credentials in order to access the website content.
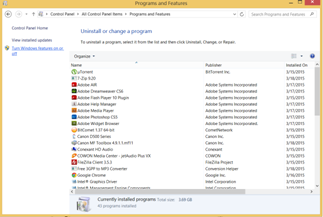
Install IIS
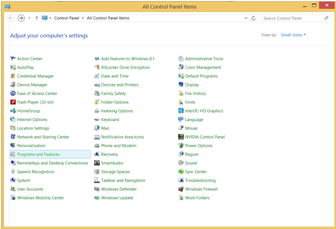
First Open Control Panel and select Program And Features
In Program and Features Window Select Turn Windows Features On or Off
Select Features To be Installed and then hit the ok button
After that a progress bar will open and IIS will be installed. Now you can open IIS Manager.
To create a virtual directory using UI
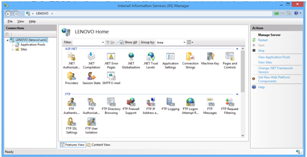
First Open IIS Manager
In the left hand portion in CONNECTIONS, click to expand the sites node. After this, opt for the site where you need to form the new virtual directory.
ACTIONS > CLICK View Virtual Directories
On virtual directories page, ACTIONS > VIRTUAL DIRECTORY
- By going to Add Virtual Directory dialog box, type in your name
- By moving to Physical path text box, enter the physical location or path of the folder of content. Browse option is enabled.
- Click Connect in order to know exactly about the credentials that are attributed with consent in order to access the path.
- Click Test Settings in order to check the settings that have been specified. This is done for the virtual directory mainly, however is optional. we specified for the virtual directory. This is optional
- Click OK.
Using Command Line
First search CMD in the Start Menu and right-click then select Run as Administrator.
Type the following command to cd \windows\system32\inetsrv then Press Enter.
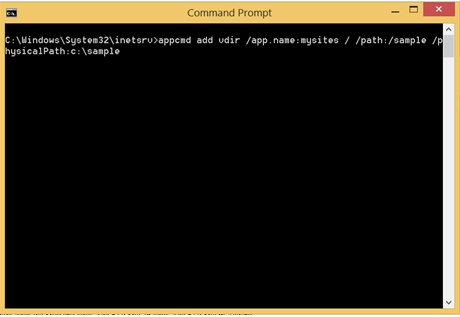
If we want to add a virtual directory to the root application in a site, use the following command:
appcmd add vdir /app.name: string / /path: string /physicalPath: string
Example
appcmd add vdir /app.name: mysites / /path:/ sample /physicalPath:c:\ sample
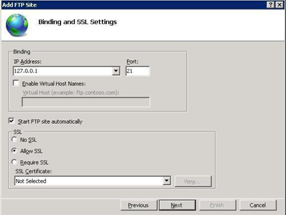
Creating a New FTP Site
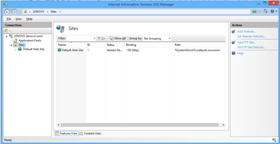
First Open IIS Manager. On the Right side is the Connections pane, click the Sites.
Right-click the Sites and click Add FTP Site, or click Add FTP Site in Actions.
When the wizard appear enter the new FTP site name and select the physical path then click next
On the next page we can select the IP and port number and also specify the SSL setting.
On the next page of the wizard we can set the authentication and authorization setting and the permission settings, then click Finish.
TASK 4 (LO3: 3.3 and 3.4)
Configure your Web Server including the following technologies/services
To configure our website and web services and FTP sites we first create a virtual directory or FTP site in the IIS and this can be done with the visage of User Interface (UI) or by using the Appcmd.exe. We can choose any of the approach that we find comfortable to work with.
After creating a new virtual directory by using user interface (UI) and following its wizards or by using the command line utility we are ready to configure various settings for our website as noted below:
- SMTP
- Authorization of certificate
- Configuring various settings
- Hosting headers
- Browsing directories
In order to perform this, a virtual server needs to be created on IIS.
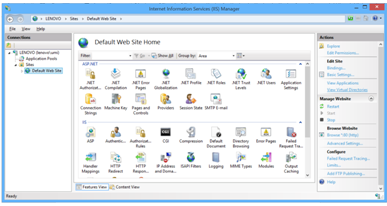
By default the directory browsing is disabled when we initially creates a new virtual directory, but if we want to enable directory browsing for our website we can change this setting simply by using the IIS Manager.
For this Start IIS Manager ? connections pane ? virtual directory that we want to unable the directory browsing for. Then in the center pane the featured view of the virtual directory double click the Directory Browsing icon or select it and hit Enter.
Choose ENABLE on the left hand portion of Alerts option in order to initiate directory browsing.
We can also specify information being displayed on the directory listing from here in the center pane.
Under the virtual directory there is an icon titled default document that we can use to configure the default documents for the virtual directory. For this first open IIS manager then select virtual directory from the connections pane that we want to edit the default documents settings. After selecting the virtual directory, choose Default Document option by double clicking on it in the center pane or select and press Enter to open default document list for the current virtual directory. On the page displayed we can add new default page for the virtual directory. We can remove a page from the default documents list of the virtual directory or we can move up or down the current specified default document list.
Configure SMTP e-mail for a Web application
We can use the following method by using UI (User interface) to configure the SMTP e-mail for a web-application running on IIS
Start the IIS Manager, in Connections pane select the web application that we want to configure the SMTP e-mail settings for. After that in the features view that is loaded in the centre of the IIS Manager User Interface. Double click the SMTP e-mail or select and press Enter to open the SMTP e-mail settings of the currently selected web application. On the SMTP view, type in email credentials of the one who is sending the message; it should be typed in the email address box. This can be concluded by opting for the most desired delivery option.There are a number of methods to do so. The quickest option to deliver messages at an instant is through the visage of delivering email to the SMTP server. If you select this option this will require a working SMTP server for which user have the credentials. Second we can choose other option provided that is Store e-mail in pickup directory. This can be used to store emails locally on a location on the disk for later delivery by any other application or an individual user such as administrator. After specifying all the required information click Apply in the Actions pane (Blondia, 2009).
Comprehensively Test the Web Server: Your testing should include documentation, eg test plan (test data, expected results, actual results); test results, vulnerability scanning and penetration testing.
|
Testing Objective |
Expected Result |
Result |
|
Test the connectivity of the server
|
The server must not have any connectivity issues. |
The server is running properly and have not connectivity issues. |
|
Test the web server is online or not |
The server should be online and be accessible to the users |
The server is online and working fine as per the requirements |
|
Test existing web can be accessed |
The website hosted in the web server should be accessible |
The website hosted in the web server is accessible |
|
Testing internal server access |
The website hosted should be access the internal server resources and have proper permissions |
The website hosted can access server internal resources and have proper access to all internal resources on the server |
|
Test access from external |
The web should be accessible from external host |
Feature is working perfectly fine |
|
Test developers have the access |
The developers should be able to access the resources available on the web server using other environment |
The developers are able to access the resources available on the server from other development environment successfully |
Testing includes the various scenarios to test and be assured that there are no deviation in implementation and it is implemented as per expectations. The web server testing includes testing the functionally of the server and the feature and facility it is providing to the users or to the developers. It is to check for any vulnerability in the server, that the server is up and running and is not offline and is ready to accept the client request that can be a web Brower or any other ftp client.
Apart from the above mentioned objectives testing also includes access server via FTP client, and to upload and downloading files from server, start stop ftp service and restart ftp service.
Configuring SSL
First Start IIS Manager and double click the Server Certificates
Then Select ‘Create Certificate Request’ or use a ‘Self-Signed Certificate’ for testing purpose.
Enter a friendly name for the certificate request and hit OK.
Now we have a self-signed certificate that we can use for testing purpose.
Next step is to set the protocol for SSL for your website. Select your website in the IIS Manager > Action pane, select Bindings > Add Site Binding
Select the Type https and ‘SampleCert’ as SSL certificate and click OK
TASK 5 (LO4: 4.1, 4.2 and D2)
Discuss how you configured Websites and services
The <cgi> is not into the installation of IIS so we have to first install it if we want to use it. For this open control panel and then open add remove programs and then select turn off and on windows features. Expand the IIS and then expand World Web services, click Application Development features and then check CGI (Gizem, Aksahya & Ayese, Ozcan, 2009).
<cgi> element servers the settings about the default settings for the CGI in IIS. It is the application setting that the IIS will be using when invoking CGI processes. It is sometimes considered as legacy application environment and because of this others are used like ISAPI and FastCGI etc.
Configuring CGI setting for a site
First start Internet Information Services (IIS) Manager. For open Control Panel Click Administrative Tools, and then select Internet Information Services (IIS) Manager.
On the left hand side, in the Connections pane, click server name, click Sites, and then move to the Website that you want to configure. Then in the home pane click CGI.
After than the home pane will gets replaced by CGI pane, here we can configure the required settings of a CGI Service and after settings all the information click Apply in Actions pane to apply changes.
To enable in-process session state by using the UI
Run IIS Manager and go to the virtual directory that is to be managed by you. Features view > Double Click Session state
After that when the Session State page is open Click in process in the Session State Mode Setting area, optionally you can configure cookie settings in the Cookie Settings on the Session State page. We can enter time in the Time-out field in the format of hh:mm:ss, optionally we can Use hosing identity for impersonation check box to use the windows authentication for remote connections. After setting all the options click Apply in the Actions pane.
Managing Windows Security
Local Users and Groups can be used to limit the users and groups to perform actions by giving rights and permission to them. Basically a right is that we authorize a user to perform a certain action on a computer. In this case, a consent is linked to an object present in the computer (Wellman, 2001)
- The user’s folder display the list of users in the computer.
- The group’s folder display the list of groups in the computer, the default local group and the local group that we create.
- When we open computer management tool we will find a panel on left hand side with the name Local Users And Groups. This is the place where we see all the users and groups that is currently in the windows system.
- There are two folders: Users and Groups.
- Below is the users screenshot
- Below is the groups screen shot
- In order to bring amendment to permissions for specific files and folders, one needs to follow the below mentioned steps:
- Locate the folder that is the source for special permissions.
- Right-click the file or folder, select Properties, and then switch to the Security tab.
- Click Advanced, and then select user
- In the Permissions box, check uncheck allow deny checkbox.
- Click apply on to subfolders if you want to.
- Click OK.
Managing IIS Security
We can set authentication in IIS in four different ways. We can configure client or server certificates that uses SSL encryption for secure connections. By setting client certificates that allows the IIS to identify client based on personal information.
IIS uses server certificates to allow client positively the server based on information in server certificate. Each of the four different methods provides separate features, so we should always select an authentication type according to our needs. The methods available for authentication is as follows
Basic authentication: it is not secure because it send the password over the network in unencrypted clear text
Digest authentication for Windows domain servers: This sends the password in encrypted mode over the network using the hash values. Hence it is secured
Integrated Windows authentication: it involve NTLM authentication protocol
.NET Passport authentication: it uses the Microsoft service that is Microsoft .NET Passport to identify and verify users.
We can change how and who are granted access to web sites under IIS for global or for each web site that is being hosted in IIS. By default anonymous user access is enabled so users don’t need to enter username and password normally (Schubert & Ginsburg, 2000).
Following steps:
Run IIS Manager; right click on the web site > properties. Open Directory Security tab or the File Security tab. open Authentication and Access Control, click the Edit to open the Authentication Methods box. After selecting authentication methods, In order to save the settings, choose the OK option and again click OK in order to shut the window.
We can apply web server permissions locally or globally. Global Web server permissions are applied at the Web Sites (parent object) node level and these are inherited by all of the Web sites, virtual directories
TASK 6 (LO4: 4.3, 4.4, M3 and D3)
To maintain and manage the health of a Web server, it is necessary to constantly monitor its performance on a regular schedule.
Here, we will be discussing the process of http login for a website; this can also be applied to an application.
Enable to start up IIS Manager first, Select the website that you want to enable logging for
Enable or disable the process of logging in at actions bar.
We can use web.config to enable logging
Logs can be created in a system monitor that helps to gather information within the prescribed tenure.
When talking about the server performance management, it refers to checking whether the server is at working condition, to check that it is delivering the required performance, whether it holds the capacity of multiple users. However, there is one major difference and that is the involvement of performance management which is used to tune the system in order to polish the performance of the system. While the capacity planning refers to laying emphasis on how to scale the site and its supportability to multiple users simultaneously. From the users point of view, a performance can be equated to the speed of accomplishing tasks and the response time of server. On clicking a hyperlink, the desired page is displayed within less than 10 seconds. And from and administrator point of view it is measured by the processing of resources and how the resources available on the server are used by the running applications (Wellman, B, (2001).
Memory
Adding more memory to the server can improve the performance but just by adding more RAM into the server won’t necessarily solve the problem and definitely not optimize server. It is necessary to determine that we are making good use of memory.
Tuning cycle can be categorized into four stages; the same is considered with redundancy till the proposed goals are attained in order to initiate the tuning.
ASP Caching
There are to special caches with other static files, the IIS Template Cache and the IIS Script Engine Cache. All the scripts run in out of process pool, and it is by default, so IIS Script Engine Cache is the part of the dllhosts this is true if we run ASP separately.
Justify the suitability of Web server tools you have used to measure and enhance internet server resources performance.
Microsoft has developed a Tool name SQLIO, to evaluate the I/O capacity of a particular configuration. As the name implies, SQLIO is a nice tool for calculating the burden of file system I/O on SQL Server performance. We have testes the test size of the file to examine the hard drive performance and how can be an incorrect size can lead us to bad results. By executing the following command
sqlIO -kR -t1 -s30 -dE -o32 -frandom -b8 -BH -LS testfile.dat
In the above mentioned command we are testing 8k random reads against the testfile.dat on the E drive. The utility will issue the 8k read request from one thread and will maintain an IO queue depth of 32
The first command gives the following result
E drive:
|
IOs/sec: |
2,681 |
|
MBs/sec: |
21 |
|
Min_Latency (ms): |
0 |
|
Avg_Latency (ms): |
11 |
|
Max_Latency (ms): |
310 |
Then we replaced the –d parameter value from E to F,and re-execute the command line tool and get the following result
F drive:
|
IOs/sec: |
19,871 |
|
MBs/sec: |
155 |
|
Min_Latency (ms): |
0 |
|
Avg_Latency (ms): |
1 |
|
Max_Latency (ms): |
16 |
By observing these results we can observer that F drive was far good performance than E drive
The sqlio utility is simple to setup and use, it provides us detailed information about the IO of disk drive and IO performance of Disk drives. It is a great utility to check IO capability of our system. It works by giving multiple IO request to the disk and it depends on what you have set in your configuration. Using SQLIO we have checked the performance of disk drives of the system name F and E respectively and found that the drive F has very good IO performance in comparison of drive E.
Plan, co-ordinate, and implement testing standards, and recommend a minimum of five changes to improve performance.
Logging Option Configuration
By default IIS logs everything that is going on. We can disable logging or we can choose a number of compulsory events to log that we are interested in.
Disable ASP debugging
We can disable asp debugging to improve the performance, It will save a great amount of power.
Limit the ASP threads per processor
The default value is 25 of ASP request handled by the server and the maximum allowed value is 100. We can set it to 50 and monitor it in IIS logs.
Modify ASP queue length property
Basically this value says that when iis will transmit server busy message to the clients (HTTP Error 503). We can update this in iis to improve performance.
Enable HTTP compression
It supports the data transfer faster between client browsers and IIS hence saves bandwidth.
References
- Blondia, C (2009). "Quality of Service through Bandwidth Reservation on Multirate Ad-doc Wireless Networks". Ad Hoc Networks Journal (Elsevier), Vol. 7, Issue 2 7 (2)
- Gizem, Aksahya & Ayese, Ozcan (2009) Communications & Networks, Network Books, ABC Publishers.
- Kozinets, R. V, (1999) “The Strategic Implications of Virtual Communities of Consumption”, European Management Journal, Vol. 17, No.3, pp.252-264.
- Wellman, B, (2001) “Computer Networks as Social Networks”, Science 293, pp 2031-2034.
- Smith, M (2002). “Tools for Navigating Large Social Cyberspaces”, Comm. of the ACM 45(4), pp 51-55.
- Schubert, P. & M. Ginsburg (2000). “ Virtual Communities of Transaction: The Role of Personalization in Electronic Commerce”, Electronic Markets 10(1), pp 45-55. International Journal of Database Management Systems ( IJDMS ), Vol.3, No.1, February 2011 107
Need Help with Your Assignment?
Get expert guidance from top professionals & submit your work with confidence.
Fast • Reliable • Expert Support
Upload NowDetails
Other Assignments
Other Solution