- support@locusassignments.com
Unit 27 Network Operating Systems Assignment
|
Program |
Diploma in Computing Systems and Development |
|
Unit Number and Title |
Unit 27 Network Operating Systems |
|
QFC Level |
Level 4 |
|
Unit Code |
K/601/0468 |
Introduction
Network operating system (NOS) helps to manage the resources effectively along with implication of efficiency and security. The report will discuss various types of NOS and related services. Various benefits of network security and disaster recovery will be discussed. Later report will design the network and network operating system for a small organization. The network operating systems assignment report will test and evaluated the implementation for capabilities in organizational operations. The report will also establish and justify the network performance baseline besides of network performance optimisation with various methods.

LO 1
1.1 Types of network operating system and services
Network operating system (NOS) is computer operating system to control and serve the client machines in network. Peer-to-peer and client-server communication in network is implemented with NOS. Majorly, following services are offered by the NOS in network:
- Printing services in network are handled and controlled to have remote access to printers, scheduling of printing jobs and to react whenever the printers are not available in network.
- Network operating system has the services to permit the access on remote file servers and to determine the set off users those can have access on remote file system associated with network (Kim and Feamster, 2013).
- Sharing of applications and internet services along with resources are under the services of NOS as it controls the remote access to user resources in network whenever the network implementation is transparent.
- NOS support routing services along with major routing protocols.
- Basic network administration tools are offered as services to administrators to manage the simple mail transfer protocols and user activities in network.
Majorly there are three types of network operating systems:
Windows servers:
Windows servers like NT and 2000 are popular operating system. Functions of directory services to manage the user accounts and information along with their credentials is key point of attraction in operating system. Operating system supports a wide range of client operating system and offer interoperability with Macintosh and Linux variants. The user authentication process in operating system is effective to guide the user to use the system. The authentication process uses alternative options to confirm the login as password and smart cards can be used to logon the system. File and printing services are in built to handle the network operations. The server is capable to offer the remote resources as native access to them so that user can work transparently with remote printers and servers (Lister, 2013). Active directory and security functions in operating systems are effective to work inside a network.
Unix/Linux servers:
Originally UNIX was created to support the protected multitasking on computers in which high performance and stability of system is also addressed effectively. High quality software, multiuser capabilities, modular architecture, easy customization and responsive graphical user interface make the system as effective choice to use in network. The strength of network to protect the data and resources from hacking attacks is high than other systems. High interoperability with windows system through SAMBA, strong security implication and authentication system are remaining major characteristics of system. However, the system has poor popularity in common users due to difficult structure of applications.
Netware
It was the first network operating system to manage the local area network but the popularity of other operating system has eaten Netware. Latest release of the NetWare also support the other technologies implemented in enterprise level network. Multiprocessing power, loadable modules and dynamic PCI configuration are key characteristics of operating system. System supports only the IP based file and printing services in network. Also the client support and interoperability is poor with latest version of windows, UNIX and mac. RSA algorithm based public key interface is used as security in network communication (Rowe.et.al.2015).
1.2 Benefits of disaster recovery and NOS security
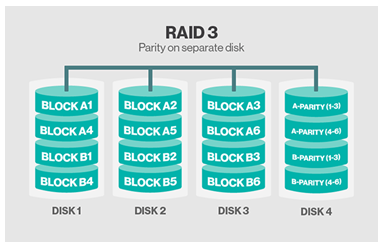
Disaster recovery means to access the resources and information in network whenever the primary resources of network connectivity go down or fails due to damage and theft. Roper strategies for disaster recovery and network security is required to ensure the availability of information. Effective disaster recovery helps the organization to retrieve the information even when the connection to server get failure as information can be saved to local backup devices or RAID storages. Major advantage is in the form of data availability as resources can be renewed but data collection and availability may affect the business operations. There may be certain options to back up the data as secondary hard disk, optical drives, magnetic taps can be used to generate copy of information but the most effective is RAID (redundant array of inexpensive disks). RAID can be used in six standard levels in which RAID devices may be organized in different manner to enhance the performance and data storage capabilities. It offers high availability and security in NOS for the information so that disaster recovery can be perform effectively (Marshall and Schrank, 2014).
Figure 1: Red level 3
(Source: RAID level 3)
1.3 Comparison of current NOS in use
|
Parameter |
Windows |
UNIX/Linux |
Mac OS X |
|
Software availability |
NOS has great support for software tools as there are many official software are available along with great collection from community. However, the community software are difficult to trust for security reasons. |
Limited set of tools are available but each tool can be marked as quality because there is official channel to verify the software and to install them. Security is high. However, only few developers has active contribution in software platform due to limited scopes in target market. |
Most trust worthy set of tools are available for operating system as highly skilled professionals has contribution in software. However, most of software are licenced and has prices. |
|
Scalability |
Each version is effective to add more users and devices to operating system. The operating system itself has compact behaviour due to proprietary licence and ownership so that scalability in term of addition of function is difficult. |
The system has open end architecture. Modularised design helps the developers to prepare the software and integration according to demands. As results, the scalability is high in term of users, devices and software integration. |
This system also has limited scalability to add functions in operating system but effective to work with a very high number of users and resources in network. Highly scalable for network uses (Sahebjamnia.et.al.2015). |
|
Maintainability |
High maintenance due to virus attacks and vulnerability possibilities. |
Low maintenance due to robust design. But regular and stable updates are required to be free from bugs. |
Low maintenance requirements. |
|
Technical support |
High from official and non-official sources |
Limited support due to number of variants. |
Limited support due to premium nature and usages policies. |
LO 2
2.1 Planning NOS to implement in scenario
Windows server is selected as the network operating system for company. Following steps are considered to follow in implementation process:
Installation:
Windows system needs to have powerful processor with or above 2.2 GHz along with 4 GB of RAM. Computer hardware must need to have storage about 50 GB of space for installation and user files in hard disk (Finn.et.al.2013).
Addressing:
Company can use Class C IP addresses between the range 192.168.168.0 and 192.168.168.24 as servers can be addressed with main address like 192.168.168.0 for web server, 192.168.168.1 for mail server and so on. Workstations and printers in network can be addressed with subnet IP addresses as it helps to make use of domain of IP addresses to connect with more devices than the actual addresses. Devices under the website design or web server as workstations can be assigned with addresses from 192.168.169.0
Security:
Password policy is prepared to have password length of at least eight character long and the combination of alphanumerical characters. Security is ensured with complicated passwords. Security patches are bugs those can help the attackers to hack the data are closed.
Disaster recovery:
RAID system is used with RAID 3 to ensure the data recovery in case of failure and damage (Maekawa.et.al.2012).
Simulation:
Cisco packet tracer and simulation program is used to simulate the network structure.
Figure 2: network simulation through cisco program
2.2 Evaluate the plan and user feedback
Plan for the operating system is effective in term of hardware selection, memory and security. There are approximately for 4 printers along with 79 workstations so that server operating system and machine must need to be powerful to handle the load and requests in effective time. Powerful processing capability of machines can be used with functions of operating system to manage the resources and users. Memory is established according to demands so that most of user files can be stored locally to provide the quick access to information. Memory is fast and parallel to process so that disaster recovery is also possible. Proper backup schedule is used to encourage the data availability and business continuity. Various network components like servers, workstations and printers are used to meet the user requirements.
Servers are safeguarded with authentication process and secure interoperability functions. Servers are also kept in isolation so that each department in company can access only the files in specific folder with proper permissions and rights (Dukes.et.al.2013). User accounts and details are managed in active directory to offer the access from any terminal in network. However the user feedback are also collected about the performance issues and risk with third party software. User’ opinion about the risk with unknown applications and files are considerable as information may be lost or corrupted through attacks. Feedback is also collected about the performance as server operating system got hanged during parallel processing of request and stops to respond for a while. However, the increase in processing power and random access memory can solve the performance issues.
LO 3
3.1 Implementation of a NOS service
Windows 7 is selected as the operating system to be installed in workstations and windows server 2008 is recommenced in servers. However the installation process for both of the operating system is same and easy.
Installation:
1. Insert windows 2008 server installation media in disk drive and configure bios to select disk drive as first boot media.
2. Save the changes by pressing F10 and reboot the system.
3. Select your language to install and proceed with next button.
3. Enter your product key and select windows server edition. Select standard edition for graphical interface and administrative tools (Stanek, 2014).
4. Accept the agreements and policies. Choose custom to install a fresh version.
5. Select tour drive or partition to install operating system.
6. Now the installation process starts. The system may reboot several times during the installation process.
7. There is no administrator account in default setting so enter the username administrator and provide password for account then login.
8. Installation complete.
Services
In order to change the user groups to have access on all printers and departmental directory, use the following steps:
1. Go to control panel, select administrative tools and then select active directory users and computers.
2. In console select users and navigate to the properties of the user account.
3. Click on ‘member of’ option and then click on group in which user needs to be like printing group or directory group etc. Make changes permanent by clicking set primary group button.
4. In this manner, file permission and directory access can be managed.
Naming
In order to assign the name and address to devices in network, organization can use the DHCP protocol to assign the dynamic IP address to computers. For naming purpose, active directory can be used to delete, rename or change password of user accounts associated to server.
3.2 Testing of user requirements
NOS implementation has addressed the user requirements as strong password policies, user account configuration and administrative permissions are managed effectively. Need of user account setting is enforced with complexity in password along with minimum requirements of characters and numbers in password. The complexity of password helps the user to fight against the brute force and assumption based attacks. User account password is configured to be expired after a regular time period so that user can enhance the security with newer passwords. Each user is included in printing group so that can access all the printers available in various offices (Sutcliffe, 2012). Users are created as standard users except the administrators so that directory access control and user account information can be managed effectively. All the standard application and resources are shared with users and administrators are powered to make changes with user permissions and rights. Few new groups are created to meet the user requirements like departmental users, global directory users and print system to assist the user in business operations.
3.3 Test results against expected results
Testing process is required to clarify the functions and role of arrangements in network. Various servers are connected to devices to meet the user requirements. Test results are given below in comparison of expectations from implementation.
|
Parameter to test |
Test result |
Expected result |
|
User friendly |
System in computers is user friend as graphical buttons and links helps to enhance the administration and other business operations. |
System must need to be according to familiarity of users so that they can accomplish work in effective manner. |
|
Security |
Excellent due to password policies as user needs to change the older password after a specific time with strong password. |
Need an option to implement user account security (Che and Maag, 2014). |
|
Sharing |
Groups are created to manage the sharing of resources effectively as printer can be accessed by anyone but directory is only accessible at members of group. |
High sharing of printing service along with dedicated directory to users and group. |
|
Management |
Easy and effective |
Easy to accomplish. |
|
Performance |
Good |
Excellent |
|
Availability |
Limited |
High |
In this manner, test results shows that implementation is effective at target users as it meets most of user requirements. However, the system must need to enhance the security of user accounts by assigning the roles and time to access in business. Performance and availability can be enhanced with addition of high power processor along with dedicated functionality of servers. As mail server and file servers needs to be separated and backup for availability purpose (Zeng.et.al.2012).
LO 4
4.1 Establish and justify the performance baseline
There are number of network monitoring tools available in market in which Microsoft network monitor, Nagios, Capsa free and GFI languard are most popular software. Microsoft network monitor can be used to establish the performance baseline as the server must need to perform certain operations under the defined quality. Following baseline is prepared:
Benchmarking: it is required to define the minimum performance and quality of the server in comparison of various software and hardware used in network. The comparison between older and newer set of components is required to test the capabilities of resources. New software and hardware must be compact in size to enhance the performance (Bonald and Feuillet, 2013).
Load test: manually the server is loaded with high number of connections and data request so that the server capability to handle the maximum load can be known. This is required to prevent the system from going down off services. Bottleneck performance issues can be covered and identified in network. Incomplete request due to connection issues must need to be logged for continuous services from broken points.
Stress test: performance baseline is defined with stress test in which the server capabilities are known to handle the number of request for the same resources. It is required to redirect and manage the stressful conditions in network to accomplish the user requests. Network must need to bench process the request or need to respond with adequate message for users.
Contention baseline: server and components in network must need to react in case the server goes down or specific resources are not available. Baseline is defined as at least thousand user requests must be accomplished on network servers. Network is prepared to redirect the request and contention to related devices to reduce the chance of failure (Mei.et.al.2013).
4.2 Monitor NOS performance against baseline
Network operating system is capable to manage the users and user request as company needs to accomplish the maximum load of 79 users on server. The server and printing resources can bench process the jobs to perform. Load testing indicated that the servers are capable to perform the user requests within the effective time and there is no conflict among two operations. Dedicated web server, mail server and file server helps to reduce the load as request from users get distribution among resources to being complete. Printers are also four in number so that operating system has low load on per device. Update to hardware and software are not so effective some time as they only need to have improve the graphical user interface not the performance. But the new improvements are also made to enhance the optimistic use of memory and processing power (Khan.et.al.2013).
In opposite situations, servers are cached at local workstations so that information can be used locally in folders to make them available whenever the server is online. With limited number of users in organization, the server and printing services can be stressed as there are fewer chances of server failures with present number of request and users. However, the number of user request specific to resource in network may result in the failure of the resource so that operating system must need to be protected with a fix range of request to queue. Remaining request must be dropped or redirected to accomplish the work.
4.3 Justify performance optimisation and updates to NOS
Performance of the network is effective to meet the organizational requirements along with user convenience as security patches in network are covered with update of software and hardware with stable release. The software bugs and holes are closed with updated configuration and settings in devices. Computers in network are enforced to use the password policies in network to secure the computer and data. Password policies are made to safe guard the systems from unwanted access. Servers are updates to optimise the performance as network users are distributed dynamically to accomplish the request at various servers. Performance is also increased with new technology in hardware changes (Chen and Yao, 2013).
Computers and storage devices in network along with communication channels are reviewed for the vulnerabilities issues as organization needs to safe the communication private and confidential from unwanted users. Security patches are installed and passwords are made stronger with new password policy.
Conclusion
The report has been discussed the various types of network operating system and services along with benefits of network security and disaster recovery. Network design and network operating systems are used to accomplish the requirements of organization. Network system and operating system is tested and recommended with some improvements. Network system is monitored for performance baselines and evaluation for optimisation in performance.
References
Bonald, T. and Feuillet, M., 2013. Network performance analysis. John Wiley & Sons.
Che, X. and Maag, S., 2014. Passive performance testing of network protocols. Computer Communications, 51, pp.36-47.
Chen, H. and Yao, D.D., 2013. Fundamentals of queueing networks: Performance, asymptotics, and optimization (Vol. 46). Springer Science & Business Media.
Dukes, L., Yuan, X. and Akowuah, F., 2013, April. A case study on web application security testing with tools and manual testing. In Southeastcon, 2013 Proceedings of IEEE (pp. 1-6). IEEE.
Finn, A., Lownds, P., Luescher, M. and Flynn, D., 2013. Windows Server 2012 Hyper-V Installation and Configuration Guide. John Wiley & Sons.
Khan, R., Khan, S.U., Zaheer, R. and Babar, M.I., 2013. An Efficient Network Monitoring and Management System. International Journal of Information and Electronics Engineering, 3(1), p.122.
Kim, H. and Feamster, N., 2013. Improving network management with software defined networking. IEEE Communications Magazine, 51(2), pp.114-119.
Lister, A., 2013. Fundamentals of operating systems. Springer Science & Business Media.
Maekawa, M., Shimizu, K., Jia, X., Sinha, P., Park, K.S., Ashihara, H. and Utsunomiya, N., 2012. Operating System. Distributed Environments: Software Paradigms and Workstations, p.259.
Need Help with Your Assignment?
Get expert guidance from top professionals & submit your work with confidence.
Fast • Reliable • Expert Support
Upload NowDetails
Other Assignments
Other Solution